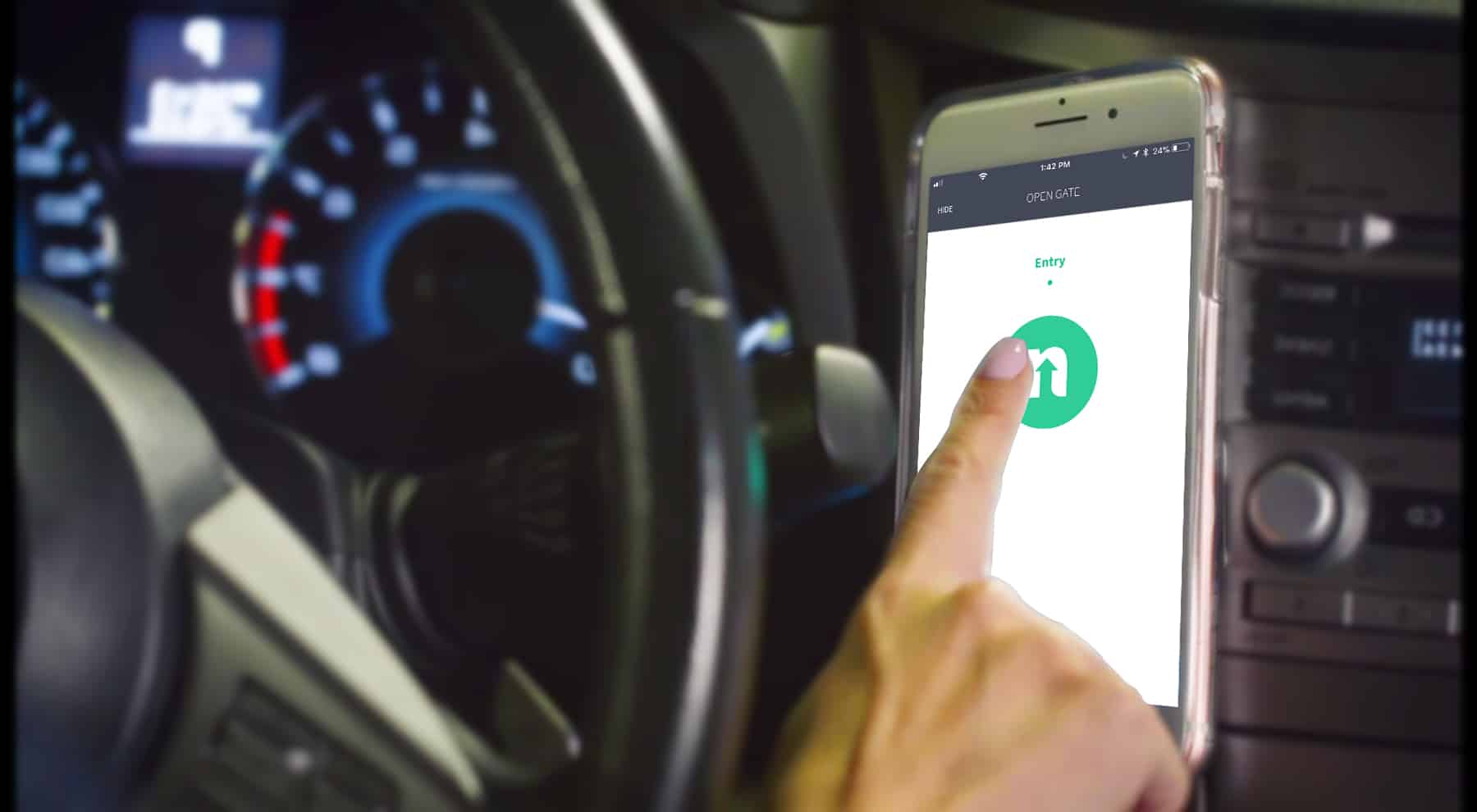
Cloning Access Credentials: Regain control of your Property’s Security
Access Control Security
Fob Cloning becomes a Security Issue in San Diego and Orange Counties
Access Professional Systems (APS) has recently become aware that companies such as InstaFob (https://www.instafob.com), ClonemyKey (https://clonemykey.com) and KeyCardNinja (https://keycardninja.com) are offering inexpensive ways to duplicate access control credentials. This puts HOAs, gated communities and any residential community with access control at risk.
How are these “DIY Fob” companies putting you at risk?
These “DIY Fob” companies have aggressive marketing campaigns and you may see their flyers being sent to your community for commercial building.
They offer mail in options and walk up kiosks at retail locations for people to get copies made, and even some local locksmiths are offering such a service.
How this impacts security
Cloning and duplicating access credentials is creating security issues. Access control is geared around knowing who, where and when. When you have people cloning fobs, the fobs mimic existing registered residents compromising the ability to effectively manage users and legitimate access into your community.
What drives people to copy fobs
There are a number of reasons why are people turning to bootlegged fobs. Here are some of the most prevalent:
- Avoiding paying the association fee for additional access credentials
- Short Term Rentals
- Subletting
- Additional rental tenants not registered with association
- Homeowners trying to avoid paying penalties for lost fobs
- Friends, family or others wanting access to parking or community facilities
What options do you have to fight back and regain control of your community and resident management?
- Monitor: Be diligent about reviewing your database of registered users. With your access system you can run reports to see if there is usage of the same fob/ credential access card at different locations at similar times or if their activity for scanning into the community has spiked.
- Keep your ear to the ground: Have your management and board members keep their ear to the ground if there are conversations about such abuse.
- Upgrade your technology
Option 1: Upgrade to Multilayer Security
We won’t get too technical, but if you want a good techy read click here https://www.hidglobal.com/sites/default/files/hid-understanding_card_data_formats-wp-en.pdf. The most common form of credential access cards and fobs are on a 26bit format and this technology is readily available and most susceptible to copy. If your community has an influx of cloned fobs, you can change out your readers to a multilayer security reader which will decrease the ability for cloning, copying and sniffing. Replacing fobs can be a herculean task, and fobs in general can be cumbersome to manage. These multi layer security readers allow for multiple bit format to be read to allow a phased roll out to take place. Further, the industry has also taken notice this security vunerability and are leaning on technology we all use, our Smartphone! So option 2…
Option 2: Smartphone Bluetooth readers
Newer access technology systems such as the ones we love ProDataKey (https://www.prodatakey.com) and OpenPath (https://www.openpath.com) have come out with smartphone access readers integrated into their cloud based access control systems. This means smartphones can replace fobs, and offer a whole range of benefits.
With this technology option, you can be sure phones will not be cloned, plus, people do not freely share their phones for others to use. Furthermore there are many additional benefits to moving to smartphone readers. Other benefits include:
- Never be left out in the cold: No one leaves home without their phone, which eliminates getting stuck out of your community because you forgot your keys or fob.
- No Hassle: You can open your door without taking your phone out of your pocket.
- No Management: Managers and properties are no longer responsible for replacing credentials when they are lost, nor for managing the distribution of credentials. When some loses their phone, you can bet that day they are at the store getting a new one.
- Compatibility: The readers still offer the traditional fob access with multilayer security if you want a backup approach for those who are not smart phone savvy.
Is your community facing this problem? It can be easier to fix than you might think. Book a call with our team to have a chat about what your upgrade options are for access control today.
Share: